New
#1
My Review of Samsung 840 EVO SSD Full Drive Encryption.
A review of the Self Encrypting Drive feature of the Samsung 840 Evo.
Industry leaders, including Samsung, are using deceptive and fraudulent language to sell “hardware based” “self encrypting” SSD's to people who want to protect their data with hardware based encryption. They are making claims that are untrue or misleading in order to peddle hardware to trusting customers.
Self Encrypting SSD's based on TCG-Opal are a big fat lie.
TCG-Opal is a scam.
Encrypts on the fly!
AES 256!
Secure Erase!
Self Encrypting Drive!
Hardware based encryption!
No impact on performance!
That is what I read on many supposedly reputable, hardware review websites about the data encryption capabilities of the Samsung 840 Evo. So I bought one. But it isn't true. Don't believe the hype.
The sites I visted had a bunch of buzz words and techie sounding slogans that mean zippo. All of the tech reviewers who reviewed the drive and stated in one way or another that the user's data on the drive would be safely encrypted using flashy sounding techno-babble should all turn in their self-awarded tech expert badges and stop writing. That includes the writers and editors from 'Tom's Hardware', 'AnandTech', YouTube tech “experts” and many, many others. Shame on you all.
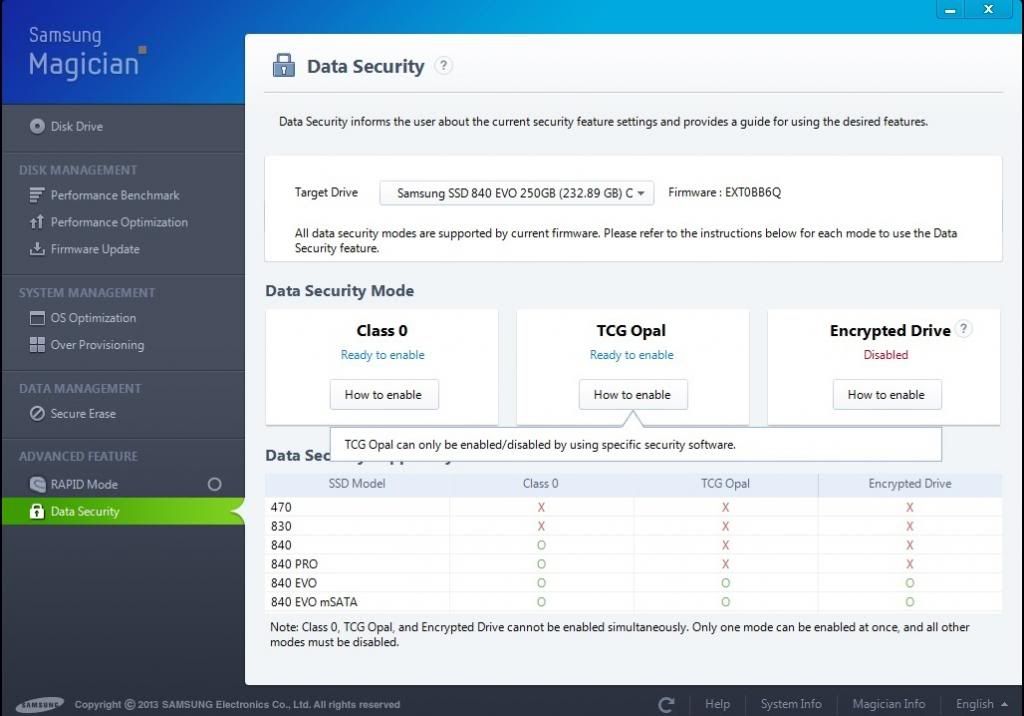
Samsung finally released their firmware update (9 December 2013)for the 840 Evo which makes the drive TCG-Opal compliant. TCG, 'The Trusted Computing Group' developed a standard for self encrypting drives like the 840 Evo. TCG appears to be an unholy trust of tech industry giants who can't seem to figure out how to actually deliver secure data encryption to the public.
What is TCG-Opal compliant? Why did I believe I would be able to securely store my data on my now TCG-Opal compliant Samsung SSD? The Trusted Computing group said I would be able too if I have a TCG-Opal compliant drive.
From the Trusted Computing Group website:
https://www.trustedcomputinggroup.or...rypting_drives
Controlled by the drive "directly". Not by the OS or a program installed on the OS. The password is independent of the BIOS. Great. That's how it should work. That's not how it really works though. But they say it does. Strange."Commonly Asked Questions and Answers on Self-encrypting Drives"
How is the access to the drive secured to allow only the Authorized user to access it? Is there a boot- up password that is entered via a BIOS dialog?
A: When the BIOS requests the Master Boot Record from the drive, the drive instead returns the pre-boot record to the user. This pre-boot record is a complete, though quite restricted OS, usually something simple like MS-DOS or LINUX. The pre-boot image requests the Authentication Credentials from the user, which are passed to and checked directly by the drive logic. If accepted, then the drive returns the MBR and the OS is loaded. Important point: This pre-boot authentication is the FIRST thing that happens and is controlled by the drive directly. This has the added advantages of not modifying the MBR, which many software encryption products do, and allowing the MBR to be encrypted like all other user accessible data.
“Many software encryption products” would include Truecypt which I have used for a couple years now. The idea then is that instead of the BIOS fetching a mini-OS from Truecrypt from the MBR on the HDD which allows me to enter a password which authenticates me and allows the drive to unlock the OS to load from my software encrypted drive....the mini-OS will load from a chip on the SSD and do the same process. Sounds good right? That's not what happens. But they say it does. Hmmm.
Also from the TCG website:
Trusted Computing Group - Solutions - Data Protection
So, controlled by the drive "directly". Great. Not by the OS or a program installed on the OS. Excellent. The password is independent of the BIOS. Just right. The way Truecrypt works. They state that vendors provide software for enterprise deployment, something not relevant to single users who buy a drive which they intend to use for their own data. Like I did.Stronger Security
Encryption always on and transparent to the user - major compliance requirement
Keys for encryption are generated in the drive and never leave the drive
User authentication is performed by the drive before it will unlock, independent of the operating system
But it turns out TCG-Opal SED-SSD's do not really have "hardware based" encryption. The industry appears to be dancing about flailing weasel words that sound very profound but upon closer examination are revealed as cheap prevarications.
Hardware based encryption. Like a chip that encrypts the data and a chip that runs firmware that requires the user to enter a password to unlock the drive and access the data. A hardware/firmware combination would qualify as "hardware based". I would buy that. The lie is that the actual interface is based on installed SOFTWARE which makes the encryption chain...SOFTWARE based.
TCG says, on their website that unlocking the drive on a TCG-Opal compliant drive is independent of both the BIOS and OS yet Samsung has produced a TCG-Opal compliant drive that does not offer a BIOS or OS or Software independent means of using a strong password for unlocking the drive. What they provide is a method for using the BIOS for a weak password that is dependent on the BIOS or a possibly stronger password method based on third party software that, naturally, runs on a software OS.
The new Samsung 840 Evo firmware from 9 December 2013 updated my drive to be TCG-Compliant yet the Samsung Magician software states that:
Samsung is lying
Trusted Computing Group is lying.
The industry is lying.
The weasels who write the reviews (you know who you are) repeated the lies. Does that make them liars too?
Well, the lazy tech writers didn't exactly lie. They merely read press releases, probably got some free hardware then regurgitated the language of the press releases to their readers without any critical examination of it. Disgraceful yes. Not deliberate lying though. They're just lazy tools. Cut and Pasters with a bucket full of benchmarking software.
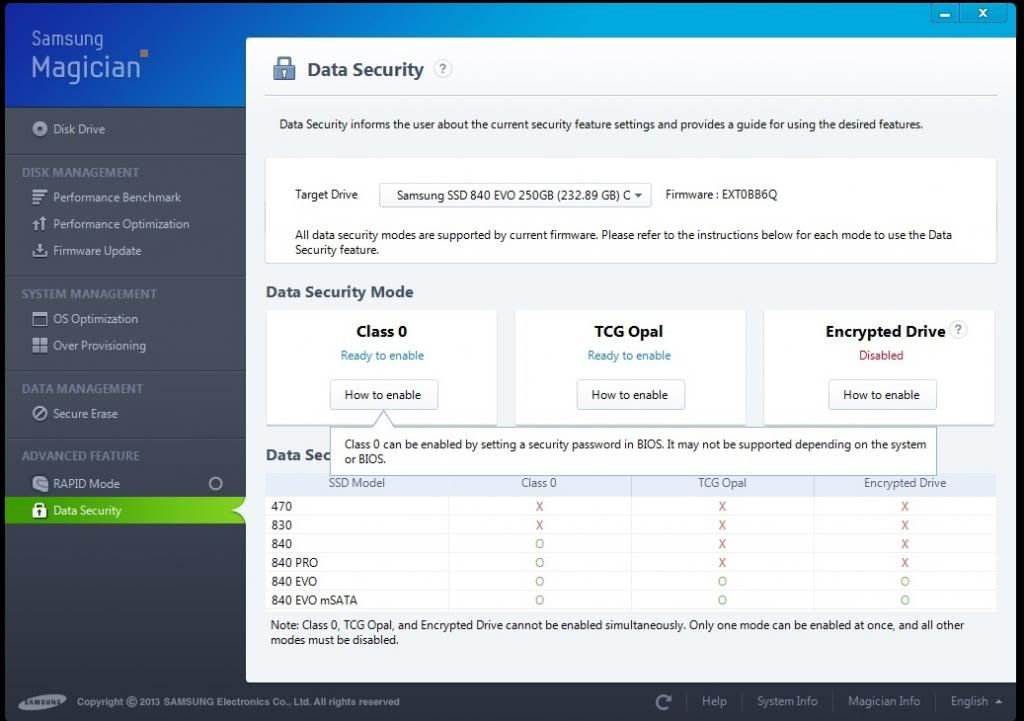
The Samsung Magician Software provides three possible levels of encryption:
Level 0 breaks TCG-Opal compliance. It is dependent on BIOS. It is also no improvement because it offers no better protection than one would get from a drive without the SED feature. It is ATA-BIOS locking/unlocking. Weak. And that only if your BIOS supports it which it probably doesn't.
Level 1 breaks TCG-Opal compliance. It is dependent on software therefore it is software based, not hardware based.
Level 2 breaks TCG-Opal compliance. It is OS dependent and also software based since it is based on bundled software included with the OS.
Levels 1 and 2 are software based meaning the installed software whether 3rd party or something bundled into the OS provides a weak link between user and hardware.
All three levels also break TCG-Opal compliance because they all depend on software, hardware, firmware, BIOS cooperation that may or may not exist on most users systems.
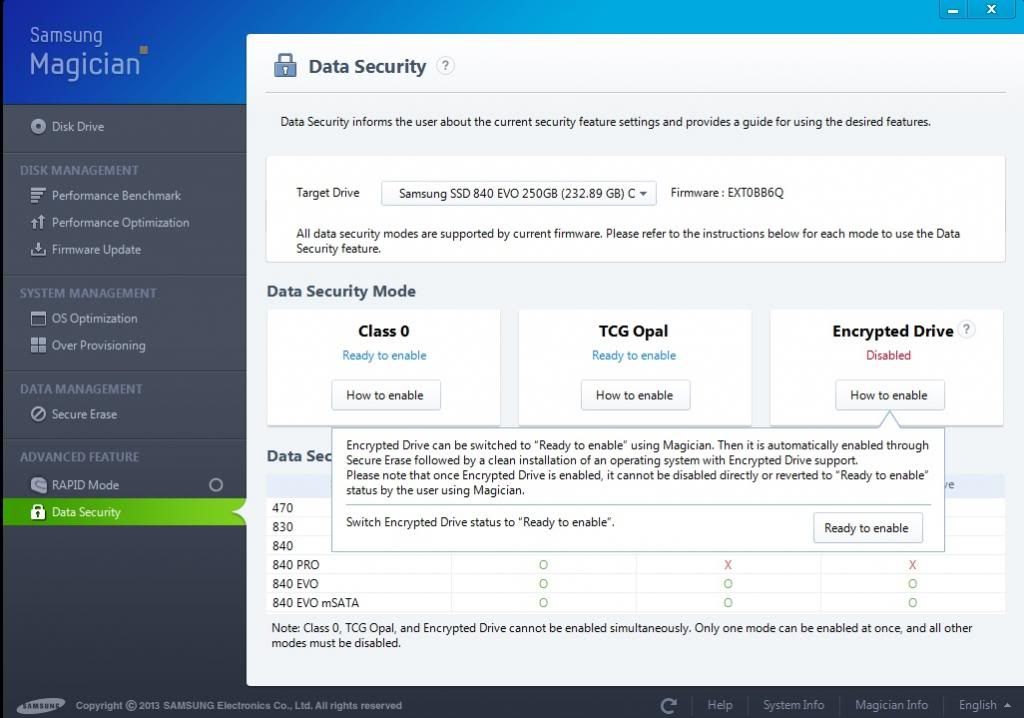
Is the Samsung 840 Evo really a SED SSD? Is it really 'hardware based' encryption? Encryption in chips is hardware based but a user must have a way to interact with the hardware to unlock the encryption to access their data. Using firmware (Free DOS or Linux on a chip) for this purpose should still qualify the encryption chain from hardware to user interface as 'hardware based'. I would call that 'hardware based' encryption. Requiring third party software to unlock the data nullifies the hardware based description though and it really then becomes software based encryption.
Think of it this way. Truecrypt is software but it uses hardware (HDD, CPU, RAM, IO Channels) for encryption, decryption, locking, unlocking data and user interface. Truecypt then could just as accurately be called “hardware based” encryption as the “hardware encryption” of SED SSD's from manufacturers like Samsung based on the apparently malleable TCG-Opal “standard” which requires installed software to function even though they claim it doesn't.
I wrote of “industry leaders”. Which ones? Go to TCG's website. They have a long list right there of TCG members. Promoters and contributors. Samsung is actually listed as an “advisor” to TCG. Really? Yes really:
Trusted Computing Group - TCG Members
The take away here is this. If you are person who intends to buy a self encrypting, solid state drive (SED SSD) because you believe your data will be safer than it would be on a non-encrypted drive...don't buy the self-encrypting drive. You will be wasting your money.
If you are someone who already uses “software” based encryption like Truecrypt but you want better performance from 'hardware based' encryption, stick with what you already have if the encryption part is important to you. You will lose the data protection if you switch to “hardware based” encryption.
If you want a really fast SSD but don't much care about protecting your data then buy an 840 Evo. The sucker is fast but the encryption is a lame joke.
If you want to gift a SSD to someone or sell it and you want to be sure your data is erased then the secure erase function in the Magician software applied to the Evo will do what it says it does. Your data will not be retrievable by anyone. I'm pretty sure of that.
If you are a compliance manager in a huge IT department then you're probably not reading this because it isn't relevant to what you do. But if you are reading this and you are looking at the enterprise level functionality of a third party software system for encrypting employee laptops for instance using Evo's or something similar you need to triple check everything you think you know about it and grill the vendor again for real because if your job depends on the data being secure after you sign off on it you are in deep trouble. The whole system is flaky as hell.
Lastly, If you are concerned there may be a “back door” built into SSD, hardware based encryption you can stop worrying. Near as I can tell there isn't even a front door.
Mongo
Last edited by MongoFongo; 12 Dec 2013 at 20:54.


 Quote
Quote