New
#1
Encrypted SSD drive...
The SSD drives have started to show up in Enterprises, where one of the requirement is full disk encryption. Full disk encryption means sector by sector encryption, that includes empty places as well.
This didn't sound good from the get go and running couple of tests, prior and after encryption, did confirm that. The system is a Dell laptop, Samsung SATA 2 SSD, running Windows 7 32-bit.
The non-encrypted SSD with AS SSD had this result:
Looks quite alright for a SATA 2 SSD.
HD Tune had similarly alright results:
The drive had been encrypted and the actual process has taken 24 minutes for a 60GBs SSD.
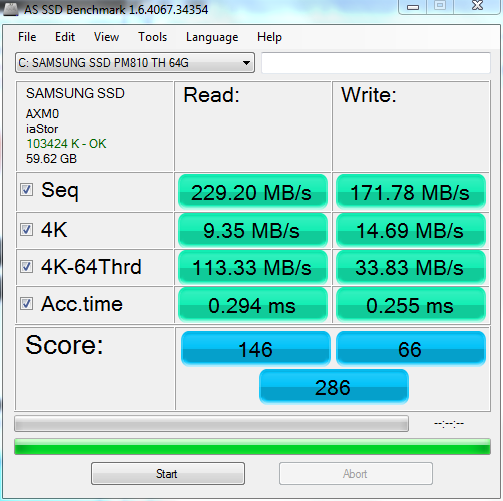
The AS SSD test results dropped like a brick, and understatement according to my wife, after encryption:
This result barely reaches 20% of the unencrypted drive performance and the test has not completed; if you notice the access time is not showing in the second AS SSD test.
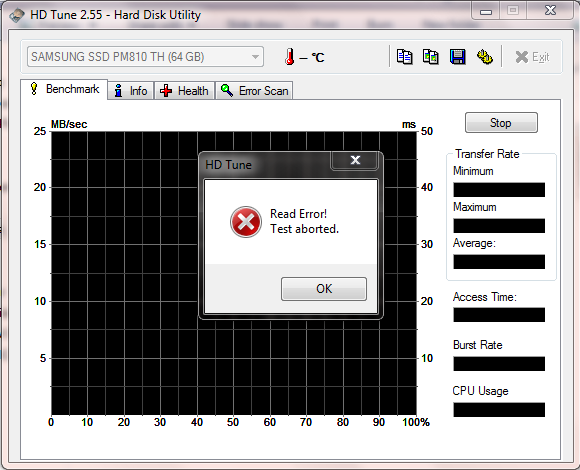
The HD Tune test of the encrypted SSD drive was even worse, it didn't even run:
This is the first time I've tested full disk encryption for an SSD drive and it is entirely possible that I've done something wrong. And no, I didn't mean encrypting the drive on the first place was wrong. As stated earlier, this is a laptop for an Enterprise where you don't have much of a choice.
So the question is...
Is it something which is normal with encrypted SSD drives and there are some tuning that can regain close to the original performance?
I'll do some more testing with HDD to see the performance hit with encryption, but I doubt that it'll be this bad.
TIA...




 Quote
Quote

 ), I can't argue the first for admins that need pretty graphs and can't write a basic vbscript to manage the TPM (/grrr). This will become less of an argument as well once MBAM (read last paragraph) becomes available, assuming the tool is as good as the others in the MDOP toolset.
), I can't argue the first for admins that need pretty graphs and can't write a basic vbscript to manage the TPM (/grrr). This will become less of an argument as well once MBAM (read last paragraph) becomes available, assuming the tool is as good as the others in the MDOP toolset.