New
#1
MBAM cannot remove "culprit" access to 5.45.64.145/5.45.69.131
A friend's Vista laptop (his wife is an AOL user, so AOL email is involved) was in need of help. I installed a proper anti-virus (Microsoft Security Essentials) as well as Anti-Malware Pro.
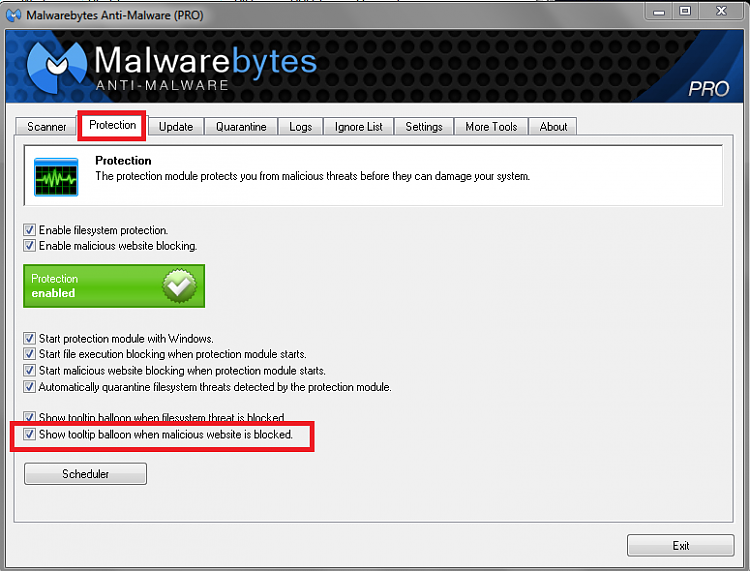
Almost immediately after installing MBAM I began to see popups about "successfully blocked access..." for two sites: 5.45.64.145 and 5.45.69.131, which are both well known malicious sites registered in the Netherlands. The access is unwanted and malicious (presumably), and the fact that MBAM blocked it is a good thing. But this happens regularly (especially when a browser or AOL is open), and each such blockage comes with a popup bubble message that must be clicked to make it disappear... and this annoying.
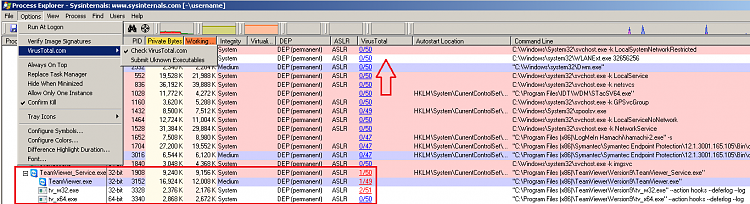
The initial scan by MBAM produced about 15 items which I purged, and then re-booted. No change. Still fairly regular popups for blocking of these two sites, whether using IE7, newly installed Firefox 26, or AOL. So whatever was found and deleted appears to have been unrelated to whatever is causing the continued ongoing access of these two IP addresses.
Cleaned out all cookies and history from IE, deleted all TEMP folders, re-booted. No change. Still fairly regular popups advising MBAM blocking these two sites. Something's still present somewhere that MBAM is not finding.
Deleted all unwanted programs and products in Control Panel, and removed/uninstalled/disabled all plugins and add-ons for IE. No change. Access to these two sites persists.
Applied all Windows Updates for Vista, including application of Service Pack 3. This installs IE8, and I further upgraded to IE9. Once again, still can't stop this accesses to the two sites. Yes, MBAM is blocking them. But there's no way to turn off the bubble-message advising that the access has been blocked, an it's just perpetually annoying to have to click on the message to make it go away or wait 10 seconds while it just fades away naturally.
Upgraded AOL from 9.1 to 9.5. Still no change. Obviously something is still "active" and attempting to contact these two sites, which has escaped detection.
Re-scanned with MBAM, and found another 3 suspect files. Deleted them, re-booted, no change. Still MBAM blocks the ongoing access of the two IP addresses.
I'm kind of at my wits end here, and looking for outside assistance. Is there a "more robust" piece of anti-malware software which might finally get to the bottom of this and locate the offending file(s) or Registry entries associated with the access of these two IP addresses?
As far as MBAM is concerned, I'd actually be willing to just accept the fact that it correctly and thankfully blocked access to these two sites "quietly and silently", rather than also bother me advising of each blockage with a popup bubble-message. But I don't see any such setting to prescribe that behavior.
Many thanks in advance for any advice or direction.
I also did run a FULL scan (as opposed to a QUICK scan), and MBAM found 2 more suspect files. But once again, deleting them and re-booting produced no change. I'm still getting ongoing attempts to access those two IP address and associated proper blocking of those attempts by MBAM.
==> I'd really like to truly remove whatever is responsible. But MBAM is obviously not finding it.


 Quote
Quote