herdProtect by Reason
Malware Detection: herdProtect, a multi-engine cloud based scanner
! Warning !Effective malware remediation often requires specialized knowledge and tools. You can use this tutorial on your own, but it is best to have the guidance of a SevenForums (SF) member experienced in malware assist you.
Follow the exact instructions of the SF member assisting you, those instructions might differ slightly from the instructions found here.
According to the author of herdProtect:
How does it work?
The scanner takes a snapshot of all the 'active' files on a user's PC. An active file is defined as currently executing on the system or has the ability to automatically execute by means of an auto-start procedure.
What you should know
The herdProtect Scanner is not a complete anti-virus solution and is more of a second opinion scanner as of this release.
1. Understanding the process and the utility
- Create a System Protection Restore Point
- Make a backup of your personal data
- Malware remediation requires specialized knowledge and tools. This guide provides the instructions to use only one tool, it does not endow you with enough information to efficiently eradicate malware on your system.
Incorrect use of any of the tools in the Malware Remediation series can seriously hamper your system. Critical system files might be infected and only a person experienced in threat remediation knows the proper methodology to use.
It is beyond the scope of any guide to provide that knowledge and experience. This guide is best used with guidance from a member who will assist you through the entire process.
- Read the online herdProtect documentation
herdProtect
2. Two install packages are offered on the herdProtect download page, a full install and a portable install3. On the Do you want to run or save ...Action Bar
Select Save
The file is placed in your default save location, normally the Downloads folder under your user profile.
4. On the The ... download has completed Action Bar
- If your user profile is an Administrator User Account:
- If your user profile is a Standard User Account:
5. Complete the initial steps to extract the program and accept any licensing agreements.
If a dialog window requests permission to run the application, Answer Yes, OK, or Run
Read the End User Licenses Agreement; Press the Accept button
Accept the default location to extract the application.
6. The final setup window is presented
WarningYou must have an active Internet connection before you launch herdProtect.
Tick
Launch herdProtect
Press the Finish button to start the scan using the default settings.
Answer Yes if prompted by a UAC dialog window
Press the Scan button.Note: This is a scan only operation, no corrective action can be taken in this mode.
herdProtect cycles through the scanning and analysis process
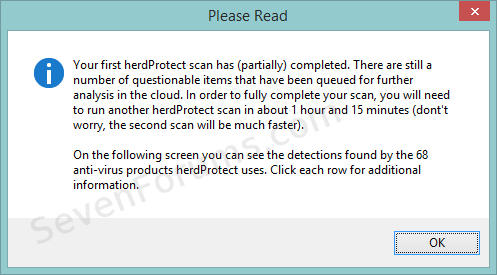
7. One of two possible Scan Results windows is presented when the initial scan has completed.
(a) Malware was not detected on your system:
This does not mean that your system is clean, it means that herdProtect did not detect any malware.
Malwarebytes Anti-Malware Free v 2.0 can provide a second opinion if you are concerned. If a SevenForums member is advising you, follow the step-by-step instructions they provide, in the order they provide.
If SF members are assisting you, please post the confirmation screen as shown above to let them know that herdProtect did not find any threats.
You might be asked post the log even though no threats were detected.
See the Attach step below and follow the log posting instructions.
You may then close herdProtect using the X on the menu bar.
Additional on-demand malware scanners might be advised by SF members.
(b) Malware was detected, detections are reported in the Scan Results window.
8. Attach the herdProtect log file to a new post on your thread.
The herdProtect log file is located in the same folder where the files were placed when extracted. The default location is
C:\Program Files\Reason\herdProtect\Portable_Scanner\Logs.
See: How to capture screenshots, upload, and attach files to your post
Please attach the most recent log file.
InformationThe logs have the following naming convention: Scan_YYYY-M-D-H-M.txt
Example: C:\Program Files\Reason\herdProtect\Scanner_Portable\Logs\Scan_2014-6-14-18-50.txt
Month and day do not have leading zeroes (i.e. 9, not 09)
Hours are in 24 hour representation (Post Meridian (PM) hour + 12)
1:30 PM is 13:30 (1 PM+12)
6:50 PM is 18:50 (6 PM+12)
Related Tutorials
Malware Detection:
- Farbar Recovery Scan Tool (FRST)
- herdProtect (this tutorial)
Malware Remediation:
- AdwCleaner
- ESET Online Scanner
- Hitman Pro (trial)
- Junkware Removal Tool (JRT)
- Kaspersky TDSSKiller: Rootkit detection and threat remediation
- Malwarebytes Anti-Malware Free v 2.0
- Microsoft Malicious Software Removal Tool
- Microsoft Safety Scanner
- Panda Cloud Cleaner
Malware Research Services:
- VirusTotal: Add 'Send to VirusTotal' to the Windows Explorer context menu
- Multiple references: Analyze suspicious files using Web based services
Real-time Anti-Virus (AV) applications:
- Microsoft Security Essentials
Note: Grayed out entries in the above list are not live tutorials, but are planned inclusions in the Malware Detection and Remediation series.
herdProtect: Malware Detection
-
New #1
This is very well done. I had no idea you wrote this up.
Fantastic job!!
A note on the herd protect tut:
if you click the cloud on the bottom left hand corner while it is trying to scan, it will test your internet connection and will see if anything is blocking it. It also will reset the proxy or lan connection to attempt a more successful connection.
Just thought you should know.Last edited by andrew129260; 02 Sep 2014 at 14:30.

herdProtect: Malware Detection
Scan for malware using the herdProtect multi-engine cloud servicePublished by Slartybart
Related Discussions

















 Quote
Quote