How to Recover a TrueCrypt Container with Corrupt Header Information
InformationTRUECRYPT is a free open source application that allows you to encrypt files, folders, partitions or even entire physical drives. It is a very useful alternative to Windows Bitlocker Drive Encryption, which is only available in Windows 7 Ultimate.
In some cases, the header information of an encrypted container/volume can become corrupted resulting in the inability to mount the container/volume and retrieve the encrypted data.
TrueCrypt allows you to attempt to recover the corrupted volume header information, thereby allowing you to access the encrypted data by mounting the container/volume as you normally would.
WarningEncrypted containers/volumes can only be recovered using this method if the volume header information is corrupted. It will NOT recover the information within the container/volume if the actual data within the container has also been corrupted, or if the encryption password has been forgotten
In order to completely protect your encrypted data, you must ensure that you have also used the other disaster recovery options mentioned in Step 3 - Disaster Recovery described here. Recovery using volume header backups should always be considered a last resort.
Symptoms of a Corrupt Volume Header
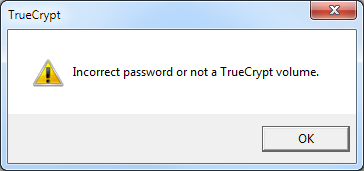
If you attempt to mount an encrypted container in which the volume header information has been corrupted, you will see this panel:
If you are sure that you have entered the password correctly, then the only reason this panel is displayed is because the header information contained in the encrypted volume has become corrupted to the degree that Truecrypt no longer recognises the container/volume.
You can attempt to 'fix' the corrupted header by mounting the encrypted volume using the backup header information.
Recovering the Volume Header
TRUECRYPT allows you to attempt to recover corrupted volume header information using two techniques:
- Using an internal or embedded backup of the volume header
- Using an external backup of the volume header
WarningIf you have changed your original encryption container/volume password, and then recovered a corrupted volume using the internal/embedded backup technique, then you can only mount the encrypted volume using this original password. This is because the internal/embedded header backup is only created once, storing the original password within the backup - subsequent changes in password are never written to the internal/embedded header backup.
If you cannot remember the original password, then you must use the external backup technique as outlined in Method 2 below. This technique assumes that you created the external backup prior to the container header becoming corrupted - refer to Step 3 - Disaster Recovery described here.
Method 1: Recovery using the Internal (Embedded) Backup
When you create an encrypted container/volume, Truecrypt automatically creates an internal backup of the volume header that is embedded within the encrypted container.
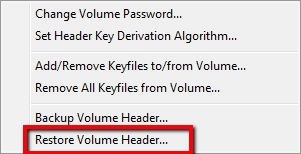
From the main Truecrypt panel, use the Select File option to select the encrypted container, and then select the Volume Tools option, as shown below.
From the pull-down list that appears, choose the Restore Volume Header option.
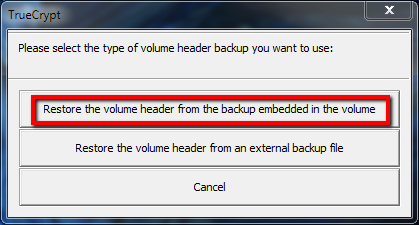
From the pop-up panel, select the first option (the internal backup of the volume header)
Now enter the password that you used when you first created the encrypted container/volume.
In the Random Pool Mixing panel, move your mouse over the hexdecimal characters in a random fashion to create the HASH, and then click Continue.
After a short period, the corrupted header information of the encrypted container is replaced with the internal backup of the header. A confirmation message will be displayed. Click OK to close the message, and then proceed to mount and use the volume as normal.
Method 2: Recovery using the External Backup
If you created an external backup of the volume header as described in Step 3 - Disaster Recovery described here, you can attempt to recover the corrupt volume header from that backup.
The steps required are exactly the same as described earlier, with the exception that you choose the Restore the volume from an external backup file option as shown below.
Once you have selected that option, you will be prompted to browse to the location of the header backup you created. You will then be prompted to input your volume password, and after a few seconds you will receive a confirmation message that the header was successfully recovered, as shown below.
You can now mount and work with the encrypted volume as normal.
WarningA final word of caution : its extremely difficult to test this recovery functionality since the volume is encrypted. As such, I only recommend this method as a very last resort when you have exhausted all other means of recovery.
Regards,
Golden
TrueCrypt - Recover Corrupt Container
-
New #1
Nice job Golden. I stumbled across this tutorial and decided that it might not be a bad idea to backup the header for my TrueCrypt volume. I do have it saved on other HDDs as well, but a little extra precaution never hurt anybody.
-
-
New #3
Nice job Golden.
-
New #4
Hello all.
I encountered exactly the described issue with an USB stick with 20GB of data, and naturally got no backup stick. when encountering the corrupt volume header + reading this VERY supportive article I choosed option 1) "internal or embedded backup" which I thought would refer to the corrupt header volume embedded on the stick which can be restored by this method. But I guess it did more refer to a header backup which I should have made when creating the stick right? There was none though.
Following all the mentioned steps afterwards I could re-mount the stick by using the original PW but the complete partition with the data was gone. tried to have it checked by recovery software when mounted, to no avail. Cannot remember the exact size of the previous partition either.
Any suggestions how to recover the stick?
-
New #5
You absolutely have to create a backup of the volume header when first encrypting a drive. It should have asked you that when you encrypted the drive from the get go. It WILL be mandatory if you encrypt a system partition. Truecrypt will verify the optical media that the backup header was written to.
With a corrupt volume header and no way to restore it, you're up sh!t creek without a paddle or life preserver.
On the subject of flash media. You'll want to read the Truecrypt manual on that. In fact, read the whole manual.
It's also possible your drive is just dead. If it's a no name drive the risk is accelerated. You'd be better of creating a massive Truecrypt container on the drive and mounting that to store sensitive data. Then unmount and copy that encrypted file to other locations as a backup. No volume header involved and you'll have encrypted backups. If you use a keyfile you'd want to back that up to many locations. I'd use optical media as another source for bit integrity. Though, the keyfile should be kept hidden but in plain view. Think everyday pictures, music, videos and what have you as a source of a keyfile. Though, I read those are not too great for a keyfile, but I believe security through obscurity is a layer.
This is only for encrypted containers. If you encrypted the whole drive its self as a non system drive, then you'd want to backup the volume header upon encrypting the drive. That's why I made mention to just use an encrypted container. The backup header is inside the container its self, but the data can go wacky. So backing up those encrypted containers would be prudent to do. Use optical media, more than one flash medium like USB sticks, SD cards, use Google Drive, Box, Azure (Microsoft cloud), Amazon S3, Mega, you name it.Last edited by file3456; 13 Apr 2021 at 02:48.
-
New #6
Hi, thanks for your comments. in fact I used a container on the stick.
so no real solution? I read something about reading out byte by byte to discover where the container was and to recover the header from the container but I dont really understand what I found so far...
regards
-
New #7
Can you post a link to that?
I wouldn't trust a USB stick or a SD card for critical data. Especially if there are several hundred writes to the drive each and every single day. It's why I mention use lots of backups. One reason why I love my optical media for bit integrity and I use several cloud providers. These particular types of flash media have a finite write capability and over time can become less and less reliable for bit integrity. And they DO need a source of power every once in a great while due to bit degradation. This is true for SSDs and NVMe as well. It would be wise to swap out such drives like USB sticks and SD cards with new versions every once in a while depending on how often you use them and if they are used with sensitive or critical data. So if you use a SD card in a WIFI cam/dash cam and it's always writing to its disk, then chances are one day it'll go south sooner rather than latter. I wanted to know what the actual MTBF (Mean Time Before Failure) was for flash SD cards and found this. Lots of conjecture without reliable sources to backup the claims, but the post with 40 votes has some interesting information. The link to the website mentioned is gone, but is available at the Wayback Machine here.
So, it's conceivable that like SD cards, a USB stick can go south and I've heard of it happening. Even with SD cards. Also, a computer could make it go south with a simple voltage spike or something. Maybe there's a near by lightning storm. A voltage spike over the USB bus should effectively erase or corrupt all the data.
I'm sure forensic tools and what not could recover your data to a reliable state for password usage again, but I have no idea how to do that. Maybe that link you have will shed some light. I do have a few tools here to crack a Truecrypt volume or container, but that's by in large all brute force using some password masks of creativity or gigabytes worth dictionary word lists and what not. Password masks can be created by the gigabyte with loads of metadata about the user who's Truecrypt protected volume or drive you're trying to crack. That's why you'd want to use a keyfile. The software I have here can't crack Truecrypt, Veracrypt or Keepass files/databases with a keyfile unless you provide the keyfile. Using loads of iterations, ChaCha20 and Argon2 or Argon2i will all help further increase security. Believe me. LOL There's a website that has a downloadable Keepass database for testing your cracking ability so I naturally gave it a crack. Since the password was in one of my wordlists of Biblical proportions, I found the password in about 10 minutes. Of course, nothing was in the keepass database file as it was just for testing and hobby use.
This is why you should ALWAYS use complex and unique passwords for ALL websites and what not. Websites get hacked all the time and if that database is in clear text or can be cracked, all of those passwords end up on the Internet as "pastes." One resource (there are several) is called HaveIBeenPwned. Google that and check your email addresses. Chances are you email was already in some hacked database. It's a little cryptic, but if you control what email address you use for certain things, then you can deduce down what accounts need their passwords changed based on the email you used. In some cases, passwords aren't exposed at all, but rather emails, home addresses, phone numbers and other crap. I find it to be massively egregious when these are multi million dollar companies (I'm looking at you Facebook) and can't even encrypt their databases with sensitive customer data. Yet here I am with a crappy little website forum of my own and all the passwords are encrypted. Heck, the latest version of my forum software called phpBB uses Argon2i. To put that into perspective, phpBB relatively recently used to use bcrypt. Now, depending on how complex the password is being hashed with bcrypt can make it next to impossible to crack. Some hackers at DEFCON (A yearly Las Vegas hacker convention) tried their hand on some bcrypt hashes and were only able to crack a few. Now add Argon2 or Argon2i and you better own a cluster of some high performance GPUs because it'll never happen as of now. Well, if the password is something like, abclookatme, it'll get cracked. But if it's something like, RedDawnueecesium77^$lolz4, then it'll be next to impossible to crack. Even in bcrypt format.
Anyway... LOL I know lots and lots of crap about this stuff. And when you know it you can be more prepared to guard against being owned and tea bagged. LMAO! (Oh, I tea bagged so many players in BF2142, BF2 and COD... those were the days).
PS: When the swingers dating website Ashley Madison got hacked, its list of passwords was more than 376 thousand. That's at least a possible ~376 thousand people breaking the 10th commandment according to Biblical tradition. In another perspective, that's just more proof society is going to hell in a hand basket with fine wine and cheese.
-
New #8
Thank you Simpilot, stay fine!
TrueCrypt - Recover Corrupt Container
How to Recover a TrueCrypt Container with Corrupt Header InformationPublished by Golden
Related Discussions









 Quote
Quote