Hi KingLordFluffy.
Download and install Drivers for Atheros AR5BWB222 and Windows 7. Follow the guide Driver Install - Device Manager if needed.
Plus, you need to do some maintenance jobs. Daemon Tools, Alcohol 120% and Power Archiver Pro uses SCSI Pass Through Direct (SPTD), which is a well known BSOD causer. Uninstall Daemon Tools at first. Then download SPTD standalone installer from Disk-Tools.com, and execute the downloaded file as guided below :
- Double click to open it.
- Click this button only:
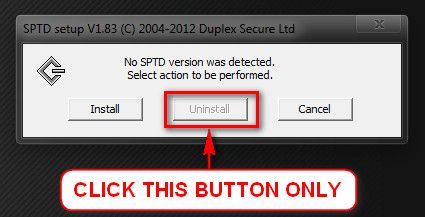
- If it is grayed out, as in the picture, there is no more SPTD in your system, and you just close the window.
Free up the startup. Windows does not need any other program to auto start with it, but the auto start programs often conflicts and causes various problems including BSODs.
- Click on the Start button
- Type “msconfig (without quotes), click the resulting link. It will open the System Configuration window.
- Select the “Startup” tab.
- Deselect all items other than the antivirus and the mouse driver.
- Apply > OK
- Accept then restart.
Let us know the results.
________________________________________________________________________________________
Code:
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 7F, {8, 80050031, 406f8, fffff80002cf9437}
*** WARNING: Unable to verify timestamp for athrx.sys
*** ERROR: Module load completed but symbols could not be loaded for athrx.sys
Probably caused by : athrx.sys ( athrx+15866d )
Followup: MachineOwner
---------
7: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
UNEXPECTED_KERNEL_MODE_TRAP (7f)
This means a trap occurred in kernel mode, and it's a trap of a kind
that the kernel isn't allowed to have/catch (bound trap) or that
is always instant death (double fault). The first number in the
bugcheck params is the number of the trap (8 = double fault, etc)
Consult an Intel x86 family manual to learn more about what these
traps are. Here is a *portion* of those codes:
If kv shows a taskGate
use .tss on the part before the colon, then kv.
Else if kv shows a trapframe
use .trap on that value
Else
.trap on the appropriate frame will show where the trap was taken
(on x86, this will be the ebp that goes with the procedure KiTrap)
Endif
kb will then show the corrected stack.
Arguments:
Arg1: 0000000000000008, EXCEPTION_DOUBLE_FAULT
Arg2: 0000000080050031
Arg3: 00000000000406f8
Arg4: fffff80002cf9437
Debugging Details:
------------------
BUGCHECK_STR: 0x7f_8
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: System
CURRENT_IRQL: 2
EXCEPTION_RECORD: fffff88011f25418 -- (.exr 0xfffff88011f25418)
ExceptionAddress: fffff80002cb6a15 (nt!DebugPrint+0x0000000000000015)
ExceptionCode: 80000003 (Break instruction exception)
ExceptionFlags: 00000000
NumberParameters: 1
Parameter[0]: 0000000000000001
TRAP_FRAME: fffff88011f254c0 -- (.trap 0xfffff88011f254c0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000001 rbx=0000000000000000 rcx=fffff88011f256c0
rdx=000000000000004f rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002cb6a15 rsp=fffff88011f25658 rbp=fffff80002e64280
r8=0000000000000050 r9=0000000000000000 r10=0000000000000000
r11=fffff88011f25570 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz ac po cy
nt!DebugPrint+0x15:
fffff800`02cb6a15 c3 ret
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002cbe169 to fffff80002cbebc0
STACK_TEXT:
fffff880`0317ade8 fffff800`02cbe169 : 00000000`0000007f 00000000`00000008 00000000`80050031 00000000`000406f8 : nt!KeBugCheckEx
fffff880`0317adf0 fffff800`02cbc632 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
fffff880`0317af30 fffff800`02cf9437 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDoubleFaultAbort+0xb2
fffff880`11f24c40 fffff800`02cbe242 : fffff880`11f25418 00000000`0000004f fffff880`11f254c0 fffff880`051d1880 : nt!KiDispatchException+0xab
fffff880`11f252e0 fffff800`02cbd8f3 : 00000000`00f80060 fffff8a0`0cda5800 00000000`00000000 00000000`00000000 : nt!KiExceptionDispatch+0xc2
fffff880`11f254c0 fffff800`02cb6a15 : fffff800`02cfdd75 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiDebugServiceTrap+0xf3
fffff880`11f25658 fffff800`02cfdd75 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!DebugPrint+0x15
fffff880`11f25660 fffff800`02cf9878 : 00000000`00000000 fffff880`05194e60 fffff880`11f25b68 fffff880`04e55353 : nt! ?? ::FNODOBFM::`string'+0xc4c2
fffff880`11f25910 fffff880`04fac66d : fffff880`051d1880 00000000`00000200 fffff880`051d1880 00000000`ffffffff : nt!DbgPrintEx+0x30
fffff880`11f25950 fffff880`051d1880 : 00000000`00000200 fffff880`051d1880 00000000`ffffffff fffffa80`04d33000 : athrx+0x15866d
fffff880`11f25958 00000000`00000200 : fffff880`051d1880 00000000`ffffffff fffffa80`04d33000 fffff880`04fcdf35 : athrx+0x37d880
fffff880`11f25960 fffff880`051d1880 : 00000000`ffffffff fffffa80`04d33000 fffff880`04fcdf35 fffff880`05194e60 : 0x200
fffff880`11f25968 00000000`ffffffff : fffffa80`04d33000 fffff880`04fcdf35 fffff880`05194e60 fffff880`11f25b68 : athrx+0x37d880
fffff880`11f25970 fffffa80`04d33000 : fffff880`04fcdf35 fffff880`05194e60 fffff880`11f25b68 fffff880`00000000 : 0xffffffff
fffff880`11f25978 fffff880`04fcdf35 : fffff880`05194e60 fffff880`11f25b68 fffff880`00000000 fffff880`11f25b68 : 0xfffffa80`04d33000
fffff880`11f25980 fffff880`05194e60 : fffff880`11f25b68 fffff880`00000000 fffff880`11f25b68 00000000`00000000 : athrx+0x179f35
fffff880`11f25988 fffff880`11f25b68 : fffff880`00000000 fffff880`11f25b68 00000000`00000000 01000018`00000800 : athrx+0x340e60
fffff880`11f25990 fffff880`00000000 : fffff880`11f25b68 00000000`00000000 01000018`00000800 745f7874`5f687461 : 0xfffff880`11f25b68
fffff880`11f25998 fffff880`11f25b68 : 00000000`00000000 01000018`00000800 745f7874`5f687461 66756264`64617178 : 0xfffff880`00000000
fffff880`11f259a0 00000000`00000000 : 01000018`00000800 745f7874`5f687461 66756264`64617178 65725f64`6c6f6820 : 0xfffff880`11f25b68
STACK_COMMAND: kb
FOLLOWUP_IP:
athrx+15866d
fffff880`04fac66d ?? ???
SYMBOL_STACK_INDEX: 9
SYMBOL_NAME: athrx+15866d
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: athrx
IMAGE_NAME: athrx.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4fd99f6d
FAILURE_BUCKET_ID: X64_0x7f_8_athrx+15866d
BUCKET_ID: X64_0x7f_8_athrx+15866d
Followup: MachineOwner
---------
7: kd> lmvm athrx
start end module name
fffff880`04e54000 fffff880`051ff000 athrx T (no symbols)
Loaded symbol image file: athrx.sys
Image path: \SystemRoot\system32\DRIVERS\athrx.sys
Image name: athrx.sys
Timestamp: Thu Jun 14 13:53:09 2012 (4FD99F6D)
CheckSum: 0039179C
ImageSize: 003AB000
Translations: 0000.04b0 0000.04e4 0409.04b0 0409.04e4


 Quote
Quote