New
#21
thank you for all guys helping:)
i've make it through.
but its wired,
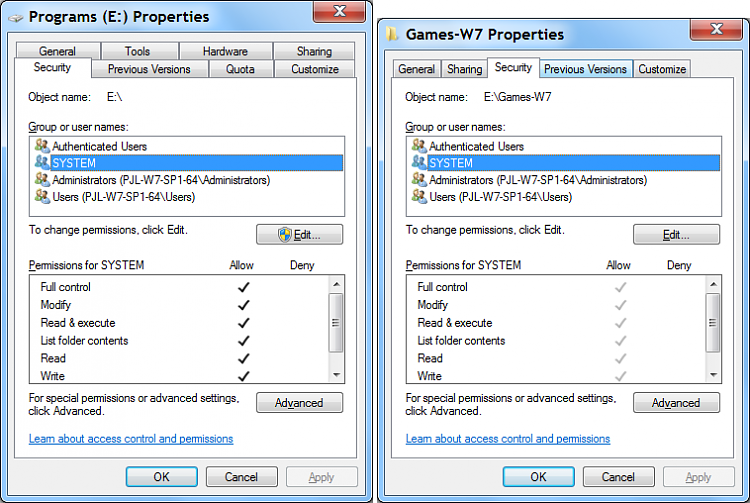
i do a test in win7 32bit that
no matter what i set a file/folder Full Control deny on Administrators Group or Administrator even SYSTEM account
using Administrator account
i still can take the permission back just uncheck the deny box without any access deny.
and i find out one more thing,
the Allow permission Administrators Group, Administrator and SYSTEM account in the testing 32bitwin7
are grey, that mean can't not remove the allow premission ,you only can add deny premission.
its same as my computer before i get the permission back.
but now i can delete the Allow permission.


 Quote
Quote