New
#21
Well... looks like the earlier "guru" post I quoted from had mis-spelled the two commands it talked of.
It's not "takedown". It is "takeown".
Here is another more accurate and similar description and example, this time to take ownership of a specific system file in order to be able to delete it.
==================================
You need to take ownership of the files, and then assign yourself rights to delete or modify the file. For this, we’ll use the command line.
Open an administrator command prompt by typing cmd into the start menu search box, and hit the Ctrl+Shift+Enter key combination.
To take ownership of the file, you’ll need to use the takeown command. Here’s an example:takeown /f C:\Windows\System32\en-US\winload.exe.muiThat will give you ownership of the file, but you still have no rights to delete it. Now you can run the cacls command to give yourself full control rights to the file:cacls C:\Windows\System32\en-US\winload.exe.mui /G geek:FNote that my username is geek, so you will substitute your username there.
At this point, you should be able to delete the file. If you still can’t do so, you may need to reboot into Safe Mode and try it again. For the filename in the example, I was able to overwrite it without safe mode, but your mileage may vary.
NOTE: the CACLS command in the above [old] example has been replaced by ICACLS
=======================================
Here's another TAKEOWN example, taking ownership for a system folder and then giving permission to SYSTEM:
takeown /f C:\Windows\System32\DriverStore\FileRepository\*.*
cacls C:\Windows\System32\DriverStore\FileRepository\*.* /G System:F
Note that the proper use of the CACLS command and its operands is very important.
========================================
take ownership of a folder:
Start a Command Prompt box (cmd) as administrator, and enter:
takeown /f /r d:\test
cacls d:\test /t /e /c /g username:F
==================================
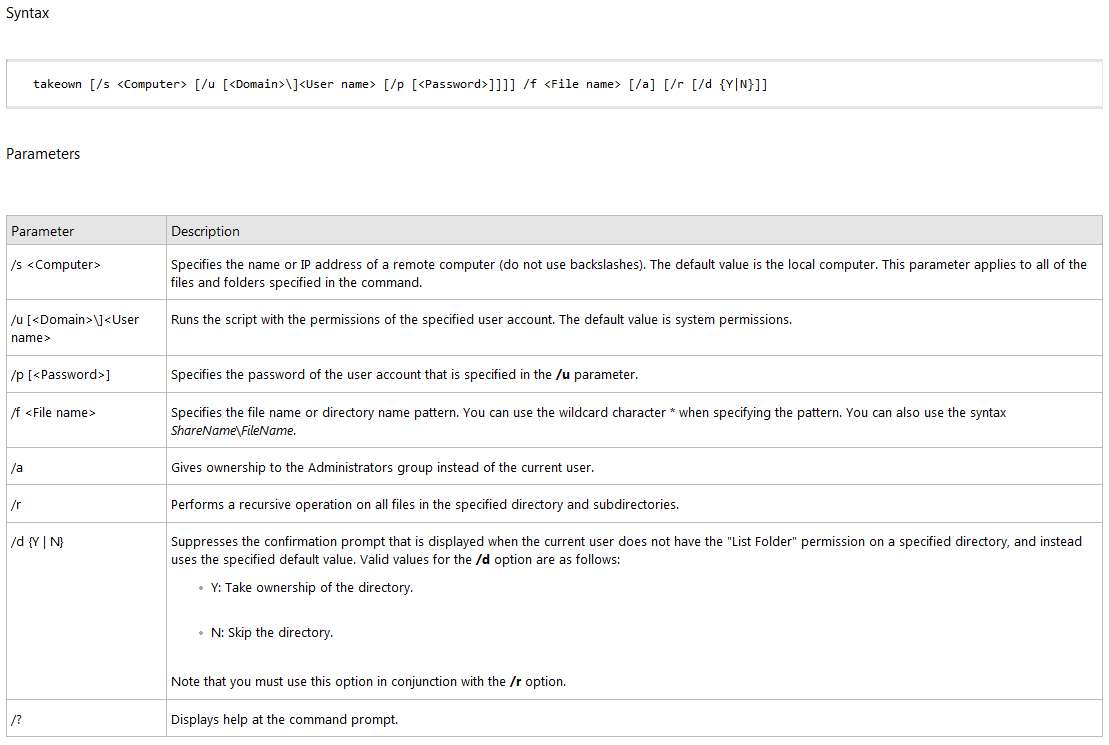
Official TAKEOWN command syntax:
TAKEOWN [/S system [/U username [/P [password]]]]
/F filename [/A] [/R [/D prompt]]
Description:
This tool allows an administrator to recover access to a file that
was denied by re-assigning file ownership.
Parameter List:
/S system Specifies the remote system to
connect to.
/U [domain\]user Specifies the user context under
which the command should execute.
/P [password] Specifies the password for the
given user context.
Prompts for input if omitted.
/F filename Specifies the filename or directory
name pattern. Wildcard "*" can be used
to specify the pattern. Allows
sharename\filename.
/A Gives ownership to the administrators
group instead of the current user.
/R Recurse: instructs tool to operate on
files in specified directory and all
subdirectories.
/D prompt Default answer used when the current user
does not have the "list folder" permission
on a directory. This occurs while operating
recursively (/R) on sub-directories. Valid
values "Y" to take ownership or "N" to skip.
/? Displays this help message.
NOTE: 1) If /A is not specified, file ownership will be given to the
current logged on user.
2) Mixed patterns using "?" and "*" are not supported.
3) /D is used to suppress the confirmation prompt.
Examples:
TAKEOWN /?
TAKEOWN /F lostfile
TAKEOWN /F \\system\share\lostfile /A
TAKEOWN /F directory /R /D N
TAKEOWN /F directory /R /A
TAKEOWN /F *
TAKEOWN /F C:\Windows\System32\acme.exe
TAKEOWN /F %windir%\*.txt
TAKEOWN /S system /F MyShare\Acme*.doc
TAKEOWN /S system /U user /F MyShare\foo.dll
TAKEOWN /S system /U domain\user /P password /F share\filename
TAKEOWN /S system /U user /P password /F Doc\Report.doc /A
TAKEOWN /S system /U user /P password /F Myshare\*
TAKEOWN /S system /U user /P password /F Home\Logon /R
TAKEOWN /S system /U user /P password /F Myshare\directory /R /A
==============================================
Official ICACLS syntax:
ICACLS name /save aclfile [/T] [/C] [/L] [/Q]
stores the DACLs for the files and folders that match the name
into aclfile for later use with /restore. Note that SACLs,
owner, or integrity labels are not saved.
ICACLS directory [/substitute SidOld SidNew [...]] /restore aclfile
[/C] [/L] [/Q]
applies the stored DACLs to files in directory.
ICACLS name /setowner user [/T] [/C] [/L] [/Q]
changes the owner of all matching names. This option does not
force a change of ownership; use the takeown.exe utility for
that purpose.
ICACLS name /findsid Sid [/T] [/C] [/L] [/Q]
finds all matching names that contain an ACL
explicitly mentioning Sid.
ICACLS name /verify [/T] [/C] [/L] [/Q]
finds all files whose ACL is not in canonical form or whose
lengths are inconsistent with ACE counts.
ICACLS name /reset [/T] [/C] [/L] [/Q]
replaces ACLs with default inherited ACLs for all matching files.
[NOTE: in following examples, the items with smilies are actually : p]
ICACLS name [/grant[:r] Siderm[...]]
[/deny Siderm [...]]
[/remove[:g|:d]] Sid[...]] [/T] [/C] [/L] [/Q]
[/setintegritylevel Levelolicy[...]]
/grant[:r] Siderm grants the specified user access rights. With :r,
the permissions replace any previouly granted explicit permissions.
Without :r, the permissions are added to any previously granted
explicit permissions.
/deny Siderm explicitly denies the specified user access rights.
An explicit deny ACE is added for the stated permissions and
the same permissions in any explicit grant are removed.
/remove[:[g|d]] Sid removes all occurrences of Sid in the ACL. With
:g, it removes all occurrences of granted rights to that Sid. With
:d, it removes all occurrences of denied rights to that Sid.
/setintegritylevel [(CI)(OI)]Level explicitly adds an integrity
ACE to all matching files. The level is to be specified as one
of:
L[ow]
M[edium]
H[igh]
Inheritance options for the integrity ACE may precede the level
and are applied only to directories.
/inheritance:e|d|r
e - enables inheritance
d - disables inheritance and copy the ACEs
r - remove all inherited ACEs
Note:
Sids may be in either numerical or friendly name form. If a numerical
form is given, affix a * to the start of the SID.
/T indicates that this operation is performed on all matching
files/directories below the directories specified in the name.
/C indicates that this operation will continue on all file errors.
Error messages will still be displayed.
/L indicates that this operation is performed on a symbolic link
itself versus its target.
/Q indicates that icacls should supress success messages.
ICACLS preserves the canonical ordering of ACE entries:
Explicit denials
Explicit grants
Inherited denials
Inherited grants
perm is a permission mask and can be specified in one of two forms:
a sequence of simple rights:
N - no access
F - full access
M - modify access
RX - read and execute access
R - read-only access
W - write-only access
D - delete access
a comma-separated list in parentheses of specific rights:
DE - delete
RC - read control
WDAC - write DAC
WO - write owner
S - synchronize
AS - access system security
MA - maximum allowed
GR - generic read
GW - generic write
GE - generic execute
GA - generic all
RD - read data/list directory
WD - write data/add file
AD - append data/add subdirectory
REA - read extended attributes
WEA - write extended attributes
X - execute/traverse
DC - delete child
RA - read attributes
WA - write attributes
inheritance rights may precede either form and are applied
only to directories:
(OI) - object inherit
(CI) - container inherit
(IO) - inherit only
(NP) - don't propagate inherit
(I) - permission inherited from parent container
Examples:
icacls c:\windows\* /save AclFile /T
- Will save the ACLs for all files under c:\windows
and its subdirectories to AclFile.
icacls c:\windows\ /restore AclFile
- Will restore the Acls for every file within
AclFile that exists in c:\windows and its subdirectories.
[NOTE: in following examples the smilies are actually : (]
icacls file /grant AdministratorD,WDAC)
- Will grant the user Administrator Delete and Write DAC
permissions to file.
icacls file /grant *S-1-1-0D,WDAC)
- Will grant the user defined by sid S-1-1-0 Delete and
Write DAC permissions to file.
============================================



 Quote
Quote