New
#1
UKASH Virus .....again :(
Hi there
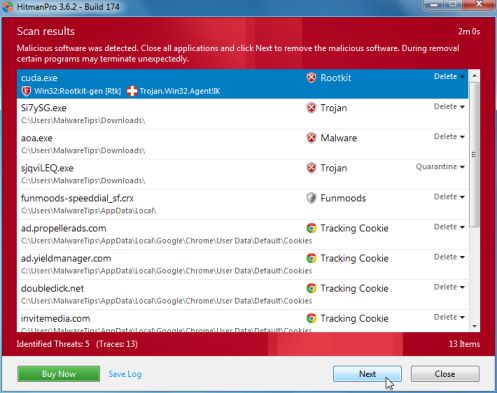
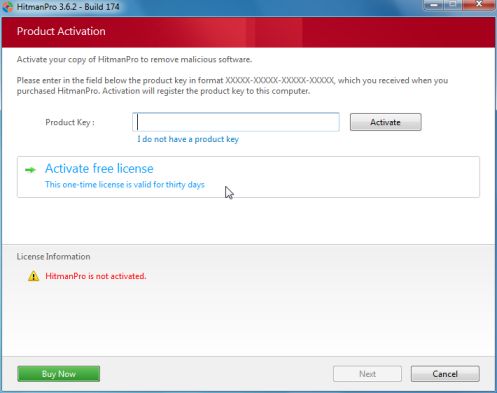
I have the dreaded Ukash virus again, exactly as per last time and last time I was kindly helped in this thread:
Ukash virus simply won't go away - help pleeeaase
Can you advise what I need to do to remove it as I guess the script in the previous thread is no longer current?
Thanks so much in advance
Darren


 Quote
Quote