New
#61
Many thanks for your summarizing the chronological essence of this thread.
Most significant "inflection point" regarding progress came on 2/2 at around 14:55PM when I ran HitmanPro and it found and removed MyWebSearch infection, which included the infected RPCSS.DLL as well as related Registry entries to launch it at system startup.
So any logs posted earlier in this thread should be viewed in the context of that 2/2 at 14:55PM turning point. Anything before that was with MyWebSearch still present, and anything after was "post-removal" by HitmanPro.
And then yesterday 2/3 per recommendation I ran SFC /SCANNOW. Apparently the fact that RPCSS.DLL was now missing from C:\Windows\System32 was discovered, and the "backup" version of RPCSS.DLL got restored from the 6002_18005 folder in C:\Windows\Winsxs. Unfortunately that version was itself the infected one. So I now had the infected version once again in C:\Windows\System32, though it appeared completely "harmless" since the necessary Registry entries to launch it into its evil state had actually been deleted on 2/2 by HitmanPro.
So I then again ran HitmanPro just to once again hopefully delete that infected version of RPCSS.DLL from C:\Windows\System32. This time HitmanPro discovered the backup version in the 6002_18005 folder (which it deleted, per its log) but it doesn't seem to have found and deleted it in C:\Windows\System32. I had thought it had disappeared from both locations following this step, but when I look now it appears to be back in C:\Windows\System32.
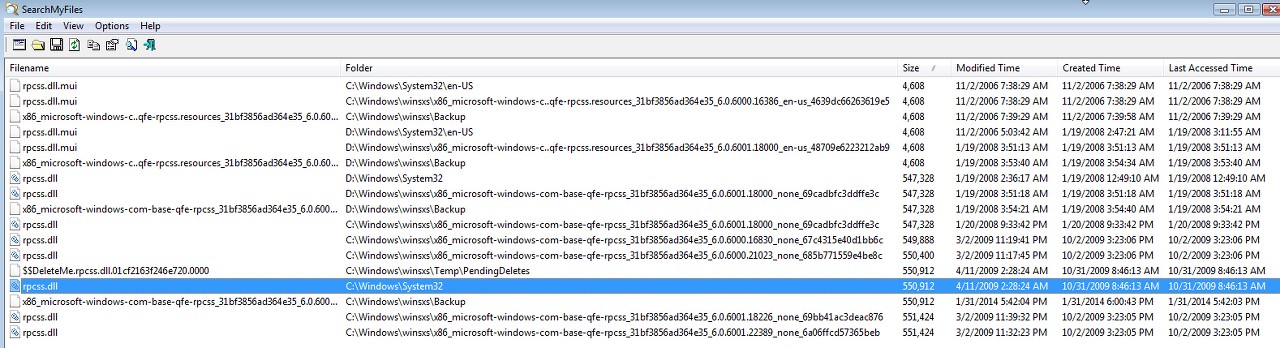
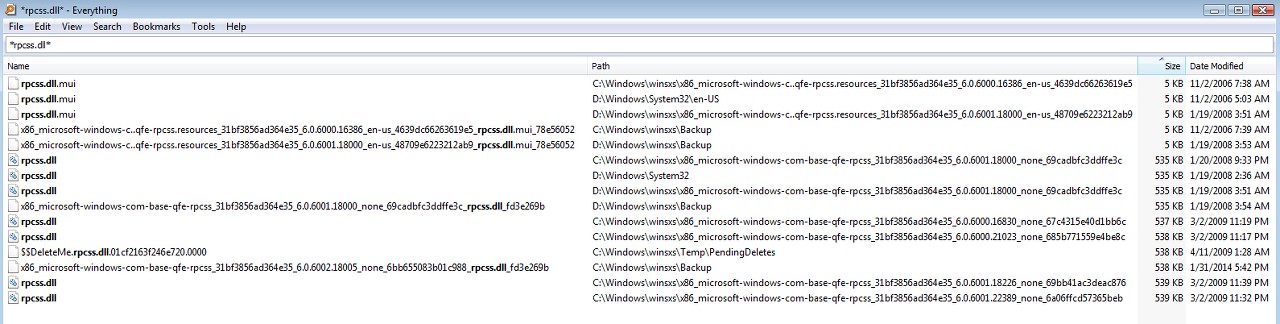
As you can see from the following screenshot, if we believe SearchMyFiles it appears that Windows is seemingly doing its own "restore" of the just-deleted version into C:\Windows\System32, perhaps caused by the effects of the SFC /SCANNOW. I admit I'm confused by the current state of things where for some reason SearchMyFiles discovers a version in C:\Windows\System32 whereas Everything and HitmanPro (just re-run again and latest log attached) do not.
Furthermore, there is still that "$$DELETEME..." infected version in \Winsxs\Temp\PendingDelete which I don't know how it got there and is not being deleted by anything.
The good news is that the infected version of RPCSS.DLL, no matter whether it's truly present or not in C:\Windows\System32, is apparently NOT ACTIVE. There are still no new "blocked IP" entries in the MBAM log, so the active malware definitely seems to be purged from the system.
A few more things observe, regarding the dates and sizes of the various versions of RPCSS.DLL now present on this Vista machine. The dates of the several infected versions of the file are misleading and inconsistent I think.
(1) Based on the D version it would appear that 547,328 is the true original size. And a date of either 1/19/2008 or 1/20/2008 is the correct original date per this Dell build.
(2) It looks like the original infected size of RPCSS.DLL was 549,888. This version is now living in backup folder 6000.16830 in \Winsxs.
(3) What looks like a second "decoy" infected version with size 549,888+512=550,400 is now living in backup folder 6000.21023 in \Winsxs.
(4) The true infected version with size 550,400+512=550,912 was previously stored in backup folder 6002.18005 but has now been deleted by a recent run of HitmanPro. But this infected version does seem to still somehow be present in C:\Windows\System32 according to SearchMyFiles, though it's not seen by Everything or HitmanPro (just re-run again). Quite a mystery here. In any case it is definitely NOT ACTIVE.
(5) Another "decoy" with size 550,912+512=551,424 is present in two backup folders, 6001.18226 as well as 6001.22389.
(6) None of the "decoys" gets detected by any scan, and they remain present. Only the 550,912 version has ever been detected by HitmanPro... and this program is currently convinced that it is no longer present.
The TDSSKiller log came from running the program in "Windows safe mode" with my friend's manual assistance. He told me the program said NOTHING FOUND. If there was a log from this execution I'm afraid it's lost or was never created. But I don't have it.The malware removal guide has more scanners in it than there are logs posted.
Can you backfill the logs for the scanners in red:
Kaspersky TDSSKiller
RKill
Malwarebytes Anti-Malware Free
HitmanPro
RogueKiller
AdwCleaner
Junkware Removal Tool
Checking the system after the clean
ESET Online Scanner.
Emsisoft Emergency Kit.
I'm attaching the requested additional logs for RKill, RogueKiller, and Junkware Removal Tool, along with the most recent HitmanPro log (from just a little while ago).
I hadn't run Emsisoft, but am doing so now. It seems fairly slow so I'll add its log to this post when if finally finishes.


 Quote
Quote
